These best practices come from our experience with azure security and the experiences of customers like you this paper is intended to be a resource f.
Azure security best practices workshop.
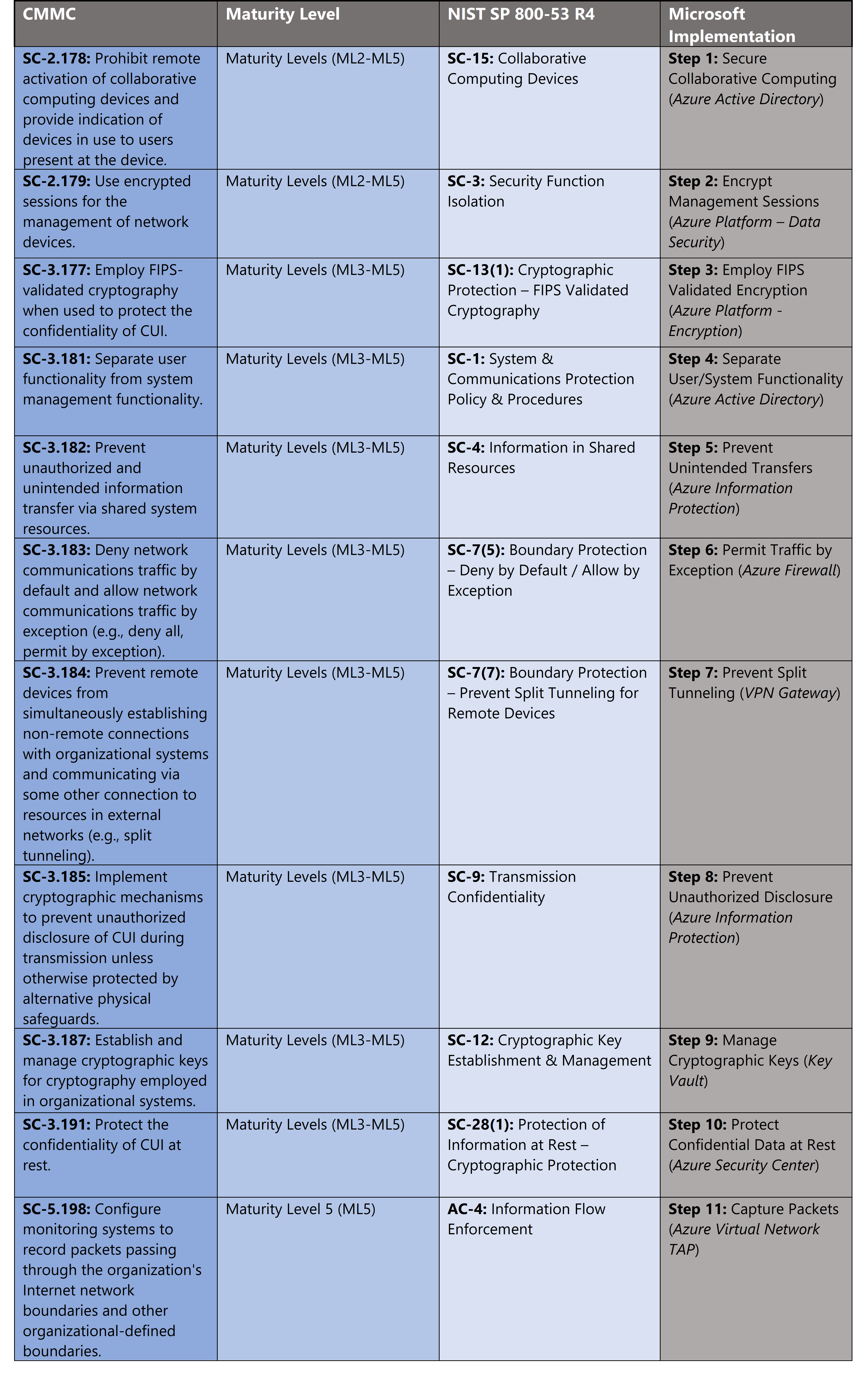
This paper is a collection of security best practices to use when you re designing deploying and managing your cloud solutions by using azure.
Wrap up with a top 10 azure security best practices for a closed workshop there is an option to focus on some parts of the topics but this needs to be agreed in advance as.
This is designed to help you increase your security posture and reduce risk whether your environment is cloud only or a hybrid enterprise spanning cloud s and on premises data centers.
Microsoft security best practices is a collection of best practices that provide clear actionable guidance for security related decisions.
The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software while reducing development cost.
The security development lifecycle sdl consists of a set of practices that support security assurance and compliance requirements.
Grant azure security center access to security roles that need it.
To protect your customer data as you run application workloads in azure kubernetes service aks the security of your cluster is a key consideration.
2 minutes to read.
7 minutes to read 13.
Security center allows security teams to quickly identify and remediate risks.
Security concepts for applications and clusters in azure kubernetes service aks 07 01 2020.
These best practices come from our experience with azure security and the experiences of customers like you.
The azure security workshop provides attendees with broad knowledge and understanding of various security features available in azure.
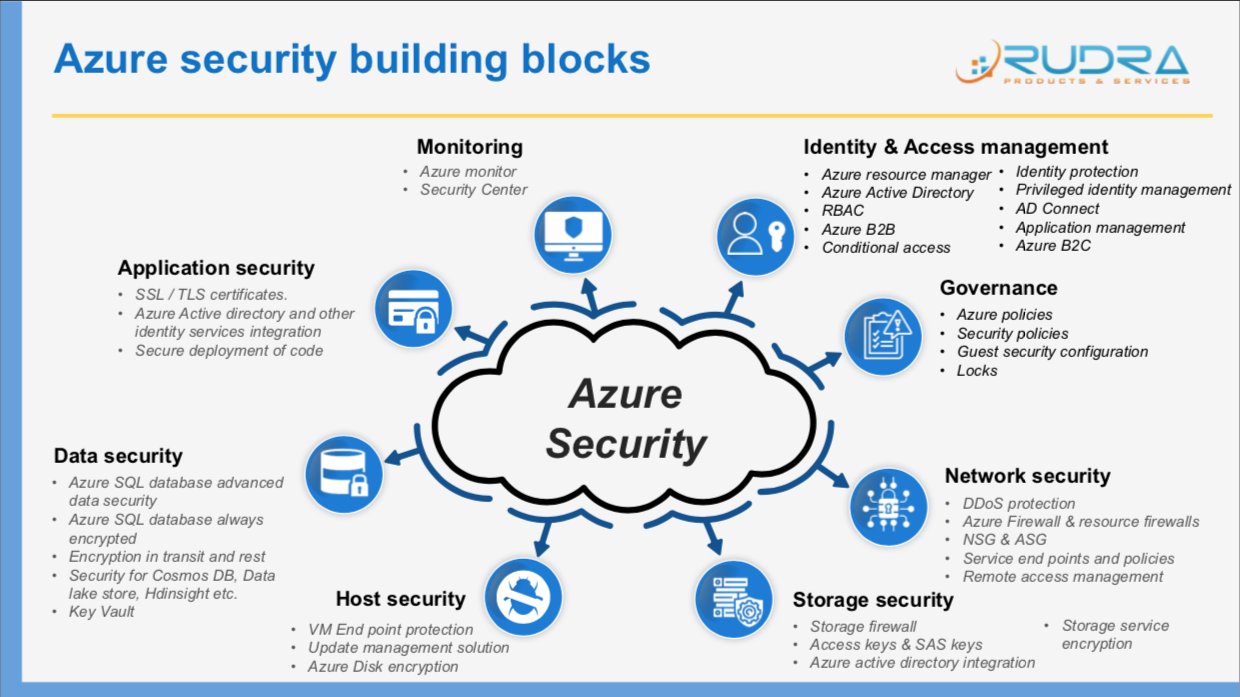
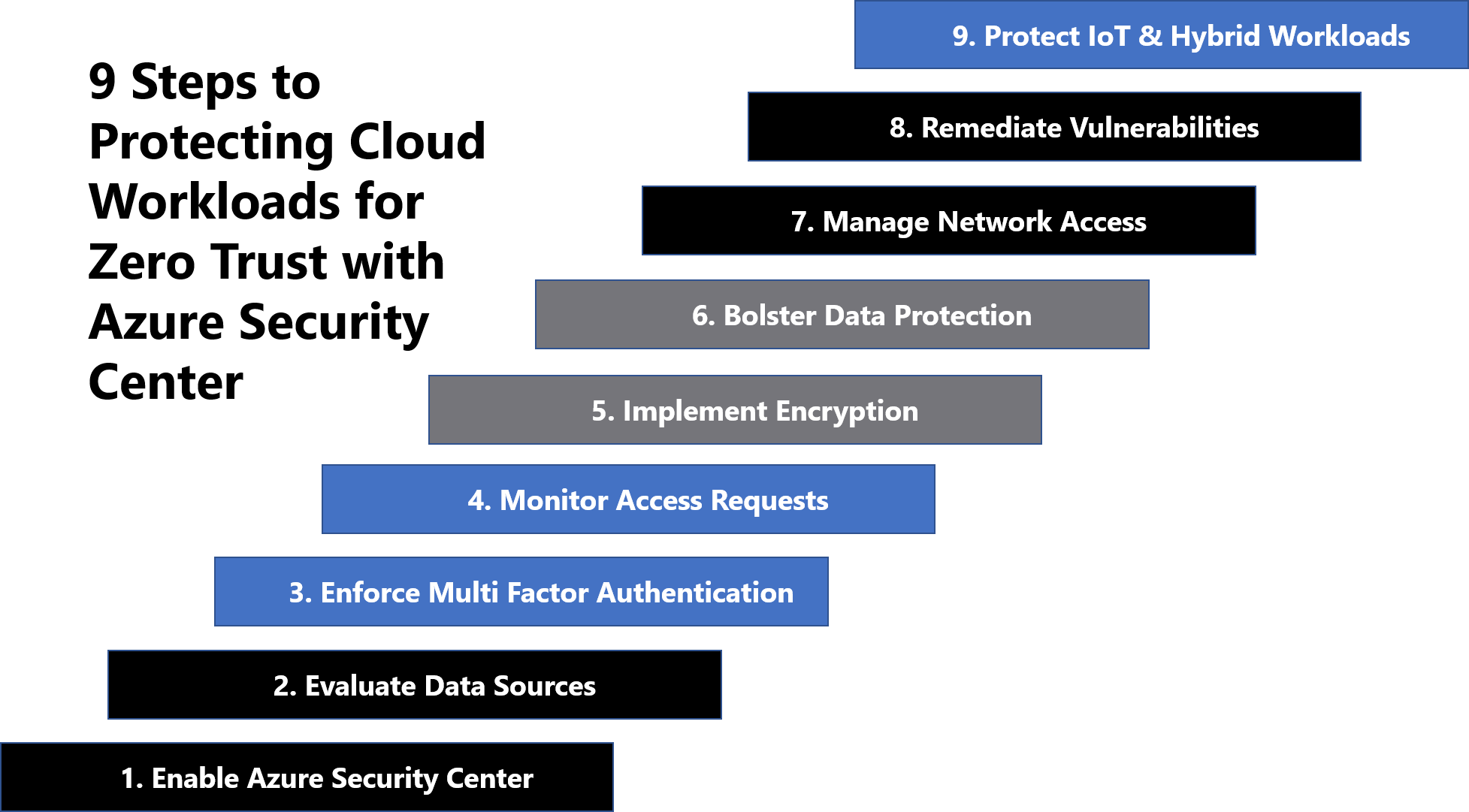
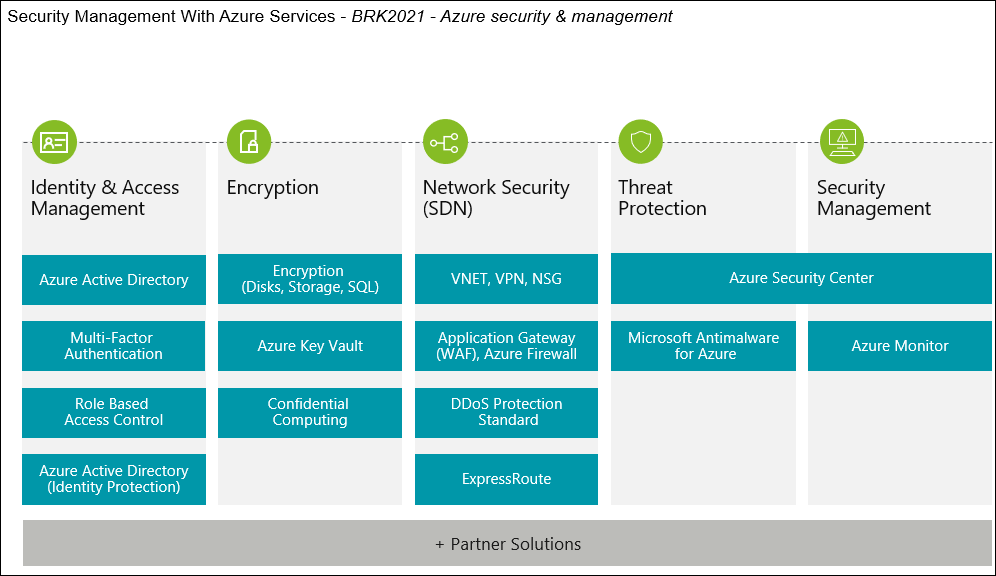
Azure security best practices and patterns.
The articles below contain security best practices to use when you re designing deploying and managing your cloud solutions by using azure.
Add security teams with these needs to the rbac security admin role so they can view security policies view security states edit security policies view alerts and.